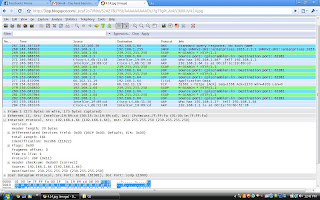
Q3. Latest Virus and its Attacks:-
One of the latest threat commonly known as Banbra.GHM which is categorised as a Trojan was detected on 10th December, 2009 poses threat on bank users. The users dealing with Brazilian banks online are the most vulnerable to this threat as their information is stolen when the access the website of their banks. This Trojan enters via email which contains few party pictures and some message in Portuguese language. This is mainly affecting computers based on of windows 2003, windows XP, windows 2000, Windows NT, windows ME and other older platforms. When the user tries to view the images attached in the email it shows an error and the Trojan enters the computer in this way. Once all the information is stored in a hidden file it is sent to the creator of the Trojan.
Panda Security (n.d) Encyclopedia Retrieved 21st December 2009
http://www.pandasecurity.com/homeusers/security-info/216004/Banbra.GMH
The other type of threat commonly now a day is Antitroy which is type of a Adware was detected on 10th December, 2009. The alarm program adware users AntiTroy tricks on your computer, so that a particular program that can removal from the market of your computer. Some areas may get AntiTroy computer when the user uses the display banners or pop-window to download. It mainly affects the systems with Windows 2003/XP/2000/NT/ME/98/95. Here is some link enable to obtain through spam, scam sites and access to a computer.
Panda Security (n.d) Encyclopedia Retrieved 21st December 2009
http://www.pandasecurity.com/homeusers/security-info/215978/AntiTroy
The other dangerous virus is called as a FakeWindows.A and technical name is Trojan and it was detected on 7th December, 2009. This is a fake in the Windows XP activation process is used to prevent the Windows product can be used as pirated software. To activate it, users will need to enter some data, including bank information. Once entered, the computer will be blocked. FakeWindows.A to reach the computer files, the file's icon with a pair of keys. However, it does not automatically mean that its own distribution. However, System does not automatically mean that their own distribution. It affects Windows 2003/XP/2000/NT.
Panda Security (n.d) Encyclopedia Retrieved 21st December 2009
http://www.pandasecurity.com/homeusers/security-info/215885/FakeWindows.A
First detection of Koobface.GQ was on 3rd December 2009 called as a worm technical name. Its main objective is through the spread of its own social networks like Face book and affects many computers. This shows on the display of information, require users to enter a few characters on the screen to avoid a computer restart. In addition, links to web sites to download malicious files, including other variants Koobface, in order to expand their distribution. It produces a link to a video of the affected primary site Face book users, will share all of their contacts. If the link, the website, similar to YouTube's (in fact YuoTube) Display: It affecting computers based on of windows 2003, windows XP, windows 2000, Windows NT, windows ME and 95 other older platforms.
Panda Security (n.d) Encyclopedia Retrieved 21st December 2009
http://www.pandasecurity.com/homeusers/security-info/215782/Koobface.GQ
Every day a new virus is coming to the market, that affect the lot of important works, in 2nd December 2009 a new Trojan was came with a common name Kates.D. This was very harmful and affected the Windows 2003/XP/2000/NT/ME/98/95/3.X platforms. It changes the configuration of Windows, monitoring network traffic, and block access to websites, publish information relating to computer security. This virus used several techniques, in order to avoid detection. It does not spread automatically using its own ways. In addition,, using a variety of techniques to prevent their detection of viruses. If it detects the computer antirootkit tool, it is to remove and registry entries to disable access to create their own.
Panda Security (n.d) Encyclopedia Retrieved 21st December 2009
http://www.pandasecurity.com/homeusers/security-info/215740/Kates.D
 Download the Nessus Vulnerability scanner from the www.nessus.org/download website it's a free version.
Download the Nessus Vulnerability scanner from the www.nessus.org/download website it's a free version.  Fill out the information for software licence agreement to register and submit it then i got a activation code through my email.
Fill out the information for software licence agreement to register and submit it then i got a activation code through my email. After activated i started Nessus server and configuration application and accept the default setting.
After activated i started Nessus server and configuration application and accept the default setting. and connect to the server by clicking connect button,When i connect with local host then i received a message that it is a first connection to the remote host. then it will ask for do u continue yes/no? Then i did yes
and connect to the server by clicking connect button,When i connect with local host then i received a message that it is a first connection to the remote host. then it will ask for do u continue yes/no? Then i did yes












 The ciphertext length of this hash is 128 bit.
The ciphertext length of this hash is 128 bit.





 This the free download option snapshot for wireshark. from the
This the free download option snapshot for wireshark. from the